Since OS X is a UNIX like many others, I usually put my environment variable settings like PATH in ~/.profile. However, for Cocoa based apps, that are not run from a terminal, this will not help. Luckily, there is a documented procedure for setting environment variables for Cocoa applications. In short, you just have to edit a plist. If it already exists on your system, just type the following in a terminal:
Syncing iPod Touch and iPhone with Linux
Ok, so I just tried out the new libimobiledevice. Installation was a breeze, using the provided OpenSUSE repository. A first run of ideviceinfo returned successfully detailed information about the attached iPod Touch. I also upgraded libgpod4. But Amarok 2.3 did not show a thing. Mounting of the iPod needed to be done manually using “ifuse ~/my-ipod-dir”. Supposedly, this happens automatically with Gnome, usin gvfs. But since I am using KDE, this is at the moment a no-go. Ok, so Amarok fails at this point in time. What about gtkpod? It works, although it throws some mysterious error message (“Eweiterte Informationen werden nicht verwendet” — wtf?), and that program is dog-slow. I though iTunes is bad, but this program is really, really slow as a snail. But here a proof of concept that I was able to sync to albums to the device:
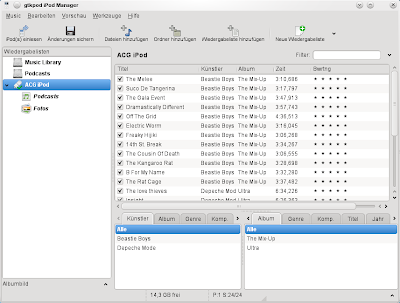
What I did not yet try is syncing contacts, notes and bookmarks. With gtkpod, you need to specify a program to do that. No idea which one that is supposed to be. Keeping my MobileMe contacts in sync with my Linux desktop would be nice, though. Also, syncing from within Amarok is mandatory for me, but does not work currently. So let’s wait and hope the situation gets better with time. So far I will continue to sync my device with OS X.
Extremely slow SMB performance over WiFi using OS X
I have an OpenSUSE machine running a Samba server to provide files to my network. Now when I use the MacBook Pro to access those files, this happens awfully slow, with 80-200 KiB per second. I never figured out why, since rsync and sftp work very fast (for WiFi at least), at speeds of around 1.2 MiB per second. Today I googled for it, and it turns out that OS X delays ACK packages. I have no clue why it does that and what good this does, but you can disable it by running:
Drag and Drop of Actions in Qt Designer 4.6.2 on OS X does not work
One more stupid bug in Qt found. When using the Designer, you can’t drag and drop QActions, if you are using the Cocoa version of Qt. The bug is described here, a fix will be available in Qt 4.6.3.
OpenCL on OS X
Emacs: autocomplete-mode

SD card reading problems
Today I was shooting some pictures using some camera and a cheap 2GB SD card. Upon returning home, I copied the pictures from the SD card to the Mac, using an old 6-in-1 card reader. After about 980 MiB of images, OS X throws a read error. Using cp in terminal yields the same result. Trying to repair the card using the hard disk utility even resulted in the system hanging. No hard freeze, but I had to power cycle it, since I was too lazy to fire up another ssh-capable machine.
After some research, I read on Wikipedia that SD cards over 1 GiB are adressed differently. It seems that older devices, such as my reader may have problems using those cards. This means I have to go buy a new reader tomorrow, I guess! Or be restricted to using only 1 Gig of the SD cards I use… Which is not a good idea for camera producing 37 MiB RAW files.
Automatic security updates for Debian
I was wondering how to configure automatic security updates for Debian. Especially for Debian stable, which I am running. Turns out it’s easy. First, you just install cron-apt. Second, you can configure it by editing /etc/cron-apt/config. I learned from some other blog, that setting one variable helps in getting actually emails for the upgrades, namely setting MAILON=”upgrade” in this file does the trick. And lastly, there is a directory /etc/cron-apt/action.d, which contains all the actions that cron-apt will execute. In there is a file named 3-download, which I changed to look as follows:
Tivoli Storage Manager: Servername not found
The infamous Tivoli Storage Manager client (a.k.a. dsmc) uses two configuration files: dsm.sys for the system wide configuration, specifying which directories to backup and so on, and the dsm.opt for the backup/restore client. The problem is, if you specify the backup SERVERNAME in both files, this will lead to problems, if they are not the same. So, e.g. I misconfigured the dsm.opt via the dsmj wizard, and had “SERVERNAME myhost” in the dsm.opt, while the dsm.sys said “SERVERNAME something.at.rwth-aachen.de”. The first entry obviously was complete bull, and confused the dsmc, so that it answered “ANS1217E Server name not found in System Options File”. Aligning both entries to the correct, real server name solves this problem.
iPhone / iPhoto syncing woes